Prove that you are in control of who can access what.
Having provable control over user access is crucial for the NIS2 and ISO27001 certifications. Elimity is the fastest way for security teams to create visibility into users and access across the IT landscape.
Better Together: How IVIP Complements IGA
This white paper explains how Identity Visibility and Intelligence Platforms (IVIP) and Identity Governance and Administration (IGA) complement each other to deliver complete identity control.Elimity mentioned by Gartner in "IVIP"
Gartner recognises Elimity as part of the newest category: Identity Visibility & Intelligence Platforms (IVIP).
How to Build Your Identity Data Fabric in 4 Steps
Can you answer these IAM questions?
✅ Which contractor accounts have to be deleted?
Collect, understand and review who can do what.
Identity Visibility
Get instant visibility into user access across critical systems. Identify your identity access risks and meet NIS2 compliance effortlessly.
Access Reviews
Run efficient access reviews, clean up risks, and involve key stakeholders with ease. Strengthen security with minimal effort.
Automated Monitoring
Continuously track user access and implement long-term governance, helping you remain in control of your identity risks.
How does the Elimity Insights platform work?
Integrate your solutions within minutes
Elimity seamlessly integrates with your most crucial cloud and on-prem applications to produce an organization-wide identity maturity report.
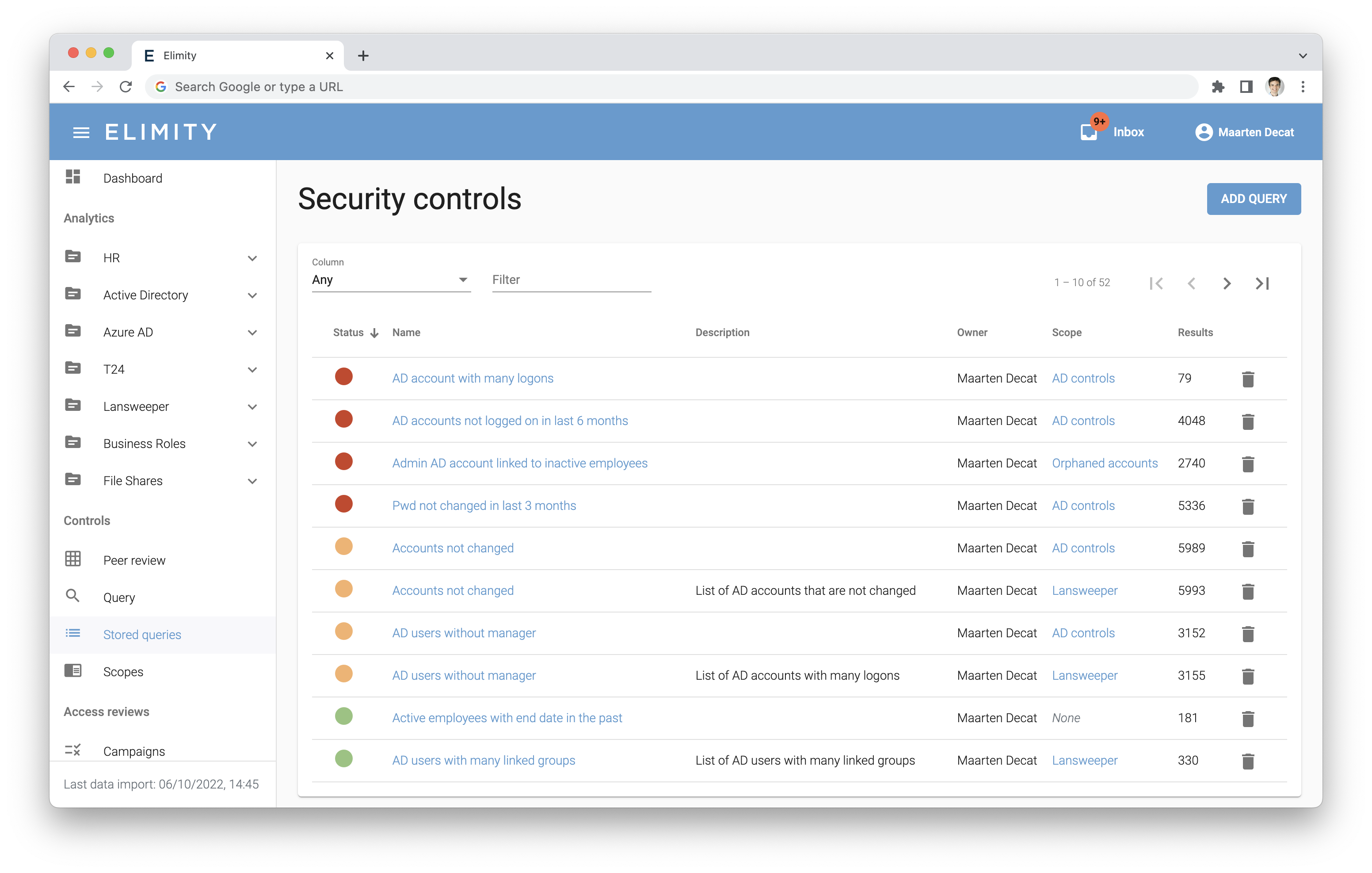
Easily understand who can access what
The first step is gaining complete visibility into your users and their permissions. Without this foundational understanding, effective access governance is nearly impossible.
Identify and clean up identity risks
Once you have identity visibility, it's crucial to involve both IT and business stakeholders in the process. Collaboratively review and clean up user accounts and accesses, ensuring alignment with your organization's security and compliance objectives.
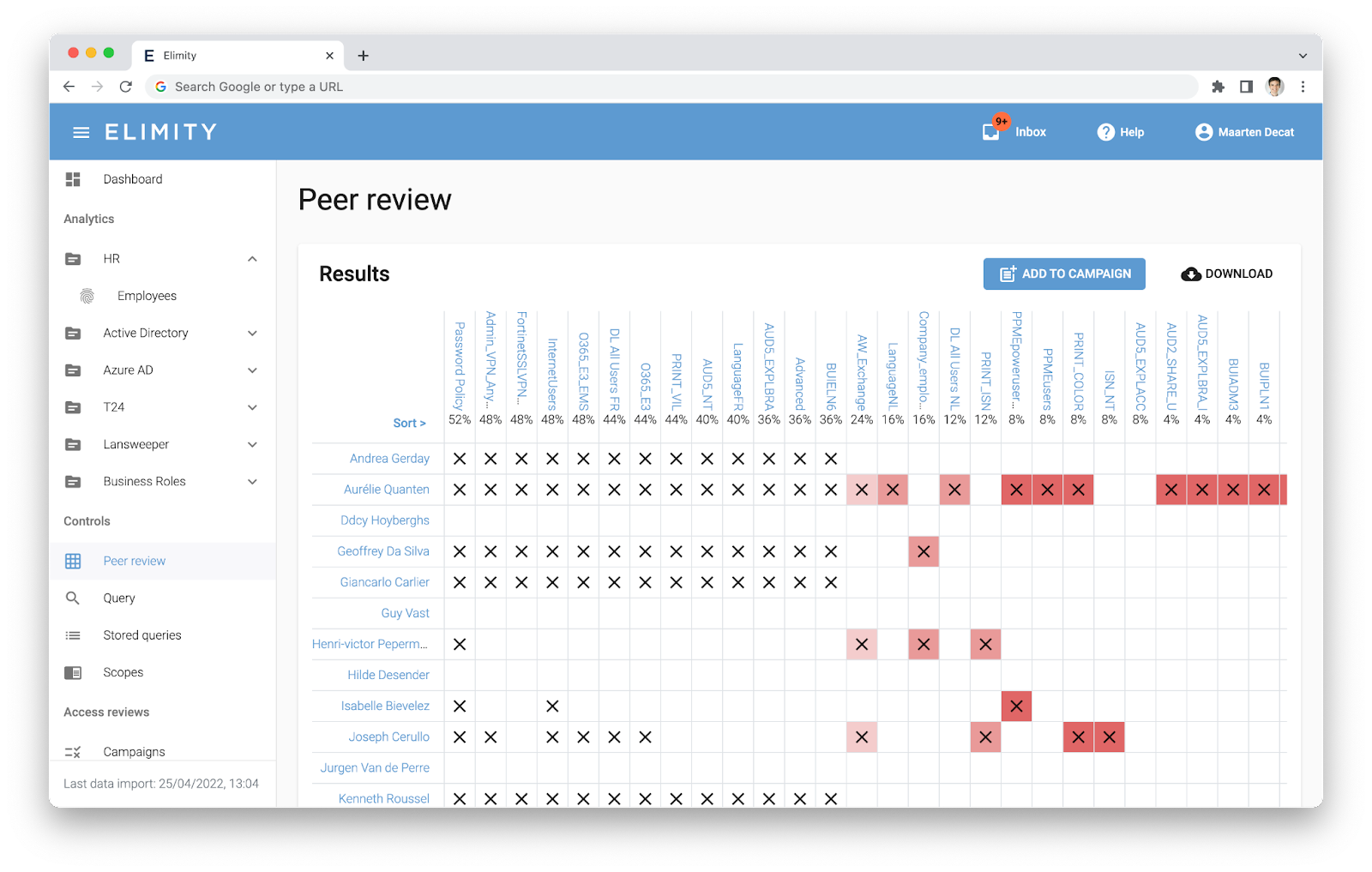
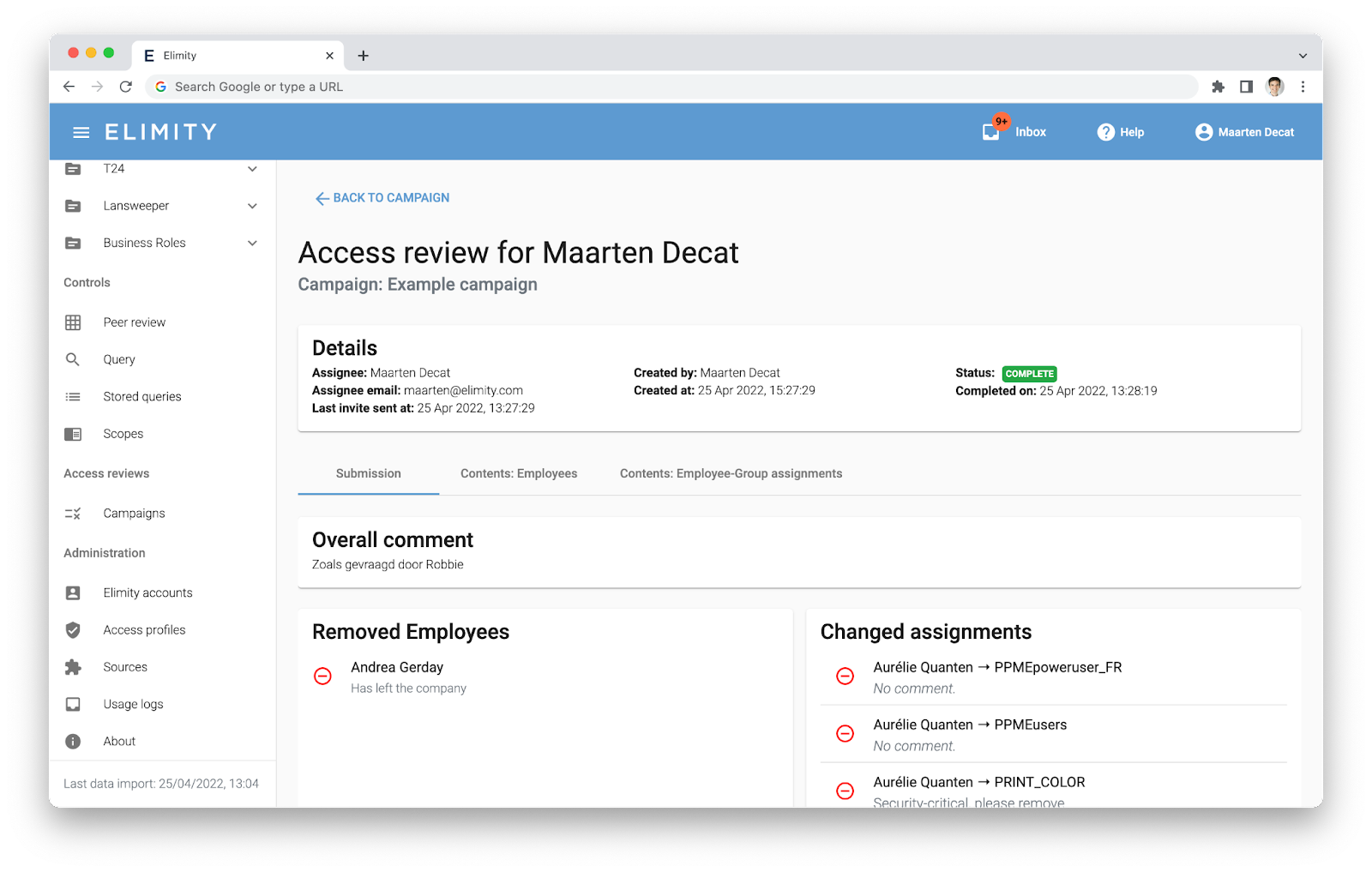
Pain-Free Access Reviews
Easily replace Excel and email for any of your access recertification campaigns. Go for visual, easy-to-use, and automated.
What our customers say
“Elimity's platform provided crucial insights regarding the security of our IT assets. Even more important, it allowed us to share the responsibility of user access with the business units."

“Monitoring user access to our organisation’s data used to be done manually. Elimity’s platform automated this process, as well as reports on the risks and controls in place, saving our security team valuable time."

"As a vendor of software for financial organisations, we are obliged to report on the security of our IT assets and data. We leverage Elimity's reporting on user access in our RFPs, without requesting time from the security team."

The 8 Identity Security Control for NIS2-Compliance
Our guide walks you through everything you need to start using KPIs to improve your IAM security.
NIS2 Questions Your Security Team Should Be Able to Answer
Insurance company takes control of user access within days.
Start Your Journey with an Identity Security Assessment
✔️ Instant Visibility into Users and Groups
✔️ +50 Identity Controls for Mature Governance
✔️ Set Up and Delivery in 2 Weeks, Not Months
✔️ NIS2 and ISO27001 Compliance Proof
✔️ Access to All Elimity Features









![[SMART MOCKUP] [GUIDES] [NIS2 GUIDE WITHOUT BACKGROUND]](https://elimity.com/hubfs/%5BSMART%20MOCKUP%5D%20%5BGUIDES%5D%20%5BNIS2%20GUIDE%20WITHOUT%20BACKGROUND%5D%20%20.png)